Hybrid working opens a potential Pandora’s Box for IT security
While debate will no doubt continue, it seems likely that working patterns have been changed irrevocably – latest figures suggest that around a fifth (22%) of the GB workforce worked at least one day a week at home, almost double the pre-pandemic level (12%).
Hybrid working brings with it new challenges and concerns particularly in terms of IT infrastructure and support with the potential heightened use of ‘bring your own device’ [BYOD] and Shadow IT.
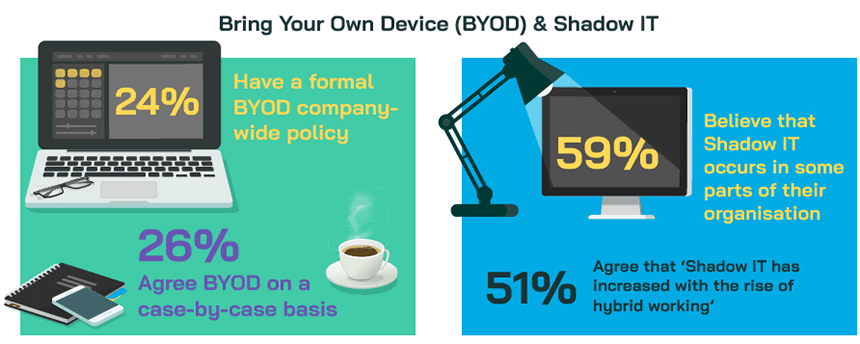
A quarter of those surveyed already have a formal BYOD company-wide policy (24%), whilst a similar proportion (26%) agree BYOD on a case-by-case basis, and 6 in 10 (59%) believe that Shadow IT occurs in at least some parts of their organisation. Half (51%) agree that ‘Shadow IT has increased with the rise of hybrid working’.
Those who use BYOD generally consider its introduction to have been successful, although just over 1 in 10 (12%) feel unable to comment – whilst this might be down to the individual respondent’s role not focusing on this specific area, it may also point to a lack of formal assessment as to the effectiveness of BYOD (particularly amongst those organisations only adopting it informally on a case-by-case basis).
BYOD is likely to place additional strain on internal IT teams
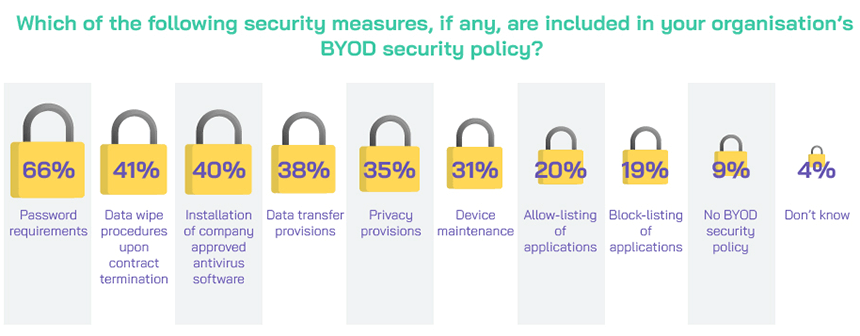
Nine in ten of those organisations using BYOD have security measures in place to cover the practice, although many of these are standard IT policies, such as password requirements and data transfer provision, which are likely to be adopted on any work device, be it employee or organisation owned. Data wipe upon contract termination, installation of company approved anti-virus software and device maintenance may raise additional BYOD challenges for any internal IT team, particularly if a variety of different devices are being used (an issue raised as a concern by over a third of those currently without a BYOD formal policy).
Amongst those without a formal BYOD policy, the key concerns centre on compliance (61%) and data removal/retrieval (53%).
BYOD further compounds the prevalence of Shadow IT, its associated risks and resourcing implications
Of those without a formal BYOD policy, a third (34%) are concerned that implementing BYOD will lead to an increase in Shadow IT within the organisation. This is a realistic expectation, given that employee-owned smartphones and computers are likely to be loaded with applications, software and tools that they use and are comfortable with, and so will want to continue accessing.
An increased prevalence of Shadow IT is clearly of concern, when the vast majority of those organisations currently with Shadow IT report experiencing security issues (80%) and/or compliance regulatory issues (74%). It is perhaps unsurprising that over 8 in 10 (84%) feel that Shadow IT results in a lack of visibility for the IT department.
Despite more efficient working and effective collaboration often being cited as a potential benefit of Shadow IT due to increased familiarity with the apps and tools being used, and improved accessibility for non-company users, 6 in 10 of those organisations with existing Shadow IT have experienced collaboration challenges as a result (59%). Almost as many have experienced Disaster Recovery issues (55%). Indeed, our mixed audience of IT and business professionals estimate that they spend on average 11% of their week addressing issues caused by Shadow IT.
Seven in ten agree that ‘Shadow IT poses a security risk to my organisation’, whilst over half (53%) disagree that ‘the advantages of Shadow IT outweigh the challenges’ (against just over a quarter agreeing – 27%).

Mitigating risk must be the focus
It is probably too late to put the genie back in the bottle: with 59% reporting some occurrence of Shadow IT in their organisation, and a quarter (26%) saying it extends across the majority or all departments, the focus must surely be on mitigating any risks posed – especially if hybrid working and BYOD are likely to continue unabated.
Central to mitigating risk is identifying the extent of Shadow IT use within the organisation. Understanding the non-company applications, software, hardware and tools that employees are turning to, and why, may help to identify gaps in the company IT provision, which can then be filled by approved versions. Risk assessments and audits can help to identify Shadow IT use which poses a serious compliance or security issue, and so allow these to be addressed before any damage is done.
Just over 7 in 10 (72%) are able to state ways in which their organisation is mitigating or planning to mitigate against the risks posed by Shadow IT, most commonly with employee education (48%) and provision of approved tools (45%).

With almost one in three (28%) reporting that they are unsure or are not currently mitigating against the risks of Shadow IT, there is still room for improvement in the management and prevention of risks.
‘The impact of remote and hybrid working on workers and organisations’, published 17 October, 2022 https://post.parliament.uk/research-briefings/post-pb-0049/
The survey findings are based on quantitative interviews conducted in December 2022 with 226 Vanson Bourne Community members. All respondents are UK based, representing a range of commercial sectors.
As a member of the Vanson Bourne Community you’ll gain access exclusive to a variety of insights reports just like this one, based on research with our members.