Understanding the Evolving Threat Landscape
The recent Snowflake credential breach, which impacted over 150 organizations, serves as a stark reminder of the critical role that Identity and Access Management (IAM) plays in defending against increasingly sophisticated cyber threats. This incident underscores a key truth: no organization, regardless of size or industry, is immune to cyber risks.
To stay one step ahead of these threats, it’s essential for organizations to embrace a proactive approach to security. As the saying goes, “hackers don’t hack in; they log in.” Robust IAM solutions are a must—but they must be informed by data and strategic insights. This is where market research becomes invaluable, offering organizations the intelligence they need to anticipate future threats and outperform competitors.
Methodology: Blending Quantitative and Qualitative Approaches
Our approach to uncovering meaningful IAM insights combined both quantitative and qualitative research methods. While quantitative data provides solid numbers that can track trends and inform decisions, the real power comes from the qualitative insights—gathering feedback directly from IT decision-makers to understand their challenges, priorities, and pain points.
By starting with qualitative research, we were able to dive deeper into the experiences and perspectives of industry professionals. These insights then guided our quantitative phase, enabling us to focus on the most relevant topics and generate more actionable data. This blended methodology gave us a 360-degree view of the IAM landscape, with both in-depth analysis and reliable metrics, ensuring our findings were both robust and credible.
Key Findings
Security is a Top Priority — Yet Organizations Struggle to Execute
Our research revealed a significant contradiction: while security remains a top priority for most organizations, many still face significant inefficiencies in their IAM practices. In interviews with IT leaders, security was repeatedly cited as a key concern. However, our quantitative data revealed that organizations often rely on a patchwork of authentication methods—an average of four across different applications. Despite this, 21% of respondents reported experiencing multiple security breaches over the past year.

This gap highlights a critical insight: while organizations believe they’re well-protected by multiple layers of security, they may still be vulnerable. Could your organization be operating under a false sense of security? It’s essential to assess whether your IAM strategy is truly up to the task in today’s threat landscape.
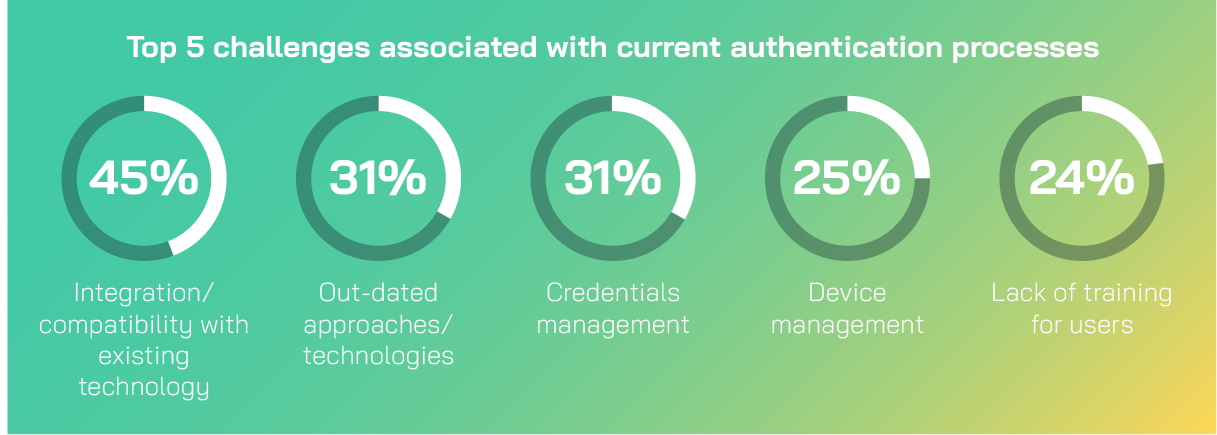
IAM Challenges: An Industry-Wide Issue
Nearly nine in ten (89%) organizations reported facing challenges with their current authentication methods. Many are still grappling with outdated technologies; 31% of respondents identified this as a key issue. This presents a prime opportunity for organizations to modernize their IAM systems and improve security posture.
The threats facing organizations are evolving rapidly, with cybercriminals becoming more sophisticated every day. Our research found that phishing (72%) and social engineering (62%) are the most common attack vectors in the identity management space, further emphasizing the need for stronger, more resilient IAM systems. Therefore, adopting robust, modern authentication methods is essential.
So what does the future hold for Identity and Access Management?
Looking ahead, our research points to passwordless authentication as a game-changer for the future of identity management. Biometric authentication, in particular, offers a powerful alternative to traditional passwords by leveraging unique physical characteristics to verify identity. Our findings show that nearly two-thirds (63%) of organizations are already using or plan to adopt fingerprint recognition. Fewer organizations are implementing facial recognition (45%) and voice recognition (36%), but the trend is clear—biometric solutions are becoming a cornerstone of IAM strategy.
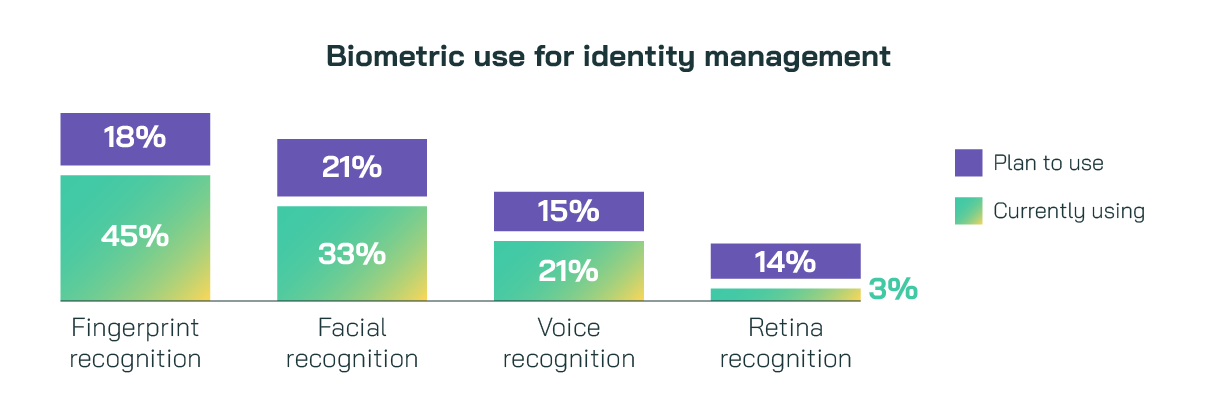
Our qualitative interviews also revealed a growing interest in multi-modal authentication — combining several biometric methods for a more secure and user-friendly experience. This layered approach not only improves protection but also reduces the chances of false positives, ensuring a smoother, more reliable user experience.

Is your organization exploring these biometrics-based methods? If not, now may be the time to consider them as a critical step in strengthening your security infrastructure.
Methodology
100 IT decision makers from the Vanson Bourne Community were interviewed in the UK in June 2024. All came from organisations across a range of sizes and private and public sectors. As a member of the Vanson Bourne Community you’ll gain access exclusive to a variety of insights reports just like this one, based on research with our members. Sign up for free here.



